Here are the Features of ManageEngine Central
- Device Onboarding
- Device Provisioning
- Risk-based Vulnerability Assessment & Remediation
- Real-time Asset Management
- Software Provisioning & Application Management
- Remote Troubleshooting
- OS Imaging & Deployment
- Reports
- Integrations
- BitLocker Management
- USB & Peripheral Device Control
- Browser Security
1. What is Device Onboarding?
Onboarding your endpoints will be the first in managing and monitoring them. Device onboarding let's IT administrators and teams to add the required devices to their scope and getting started with their endpoint management and security operations. Endpoint Central supports onboarding both traditional devices (which includes servers, desktops, and laptops) and modern devices (which includes mobile devices, Rugged devices, IoT devices, TV, laptops running on Mac; Windows 10; and Windows 11).
How to onboard devices?
To onboard a device, IT administrators should install an agent (for a server, desktop, or laptop) or enroll them to the central server (in case of a mobile device, rugged device, IoT, TV, Hololenses, Surface Hubs, laptop, or Chromebook). Endpoint Central supports a number of methods to onboard a device. Check these pages to learn about the following:
- Installing an Agent
- Enrolling a Device
2. What is Device Provisioning?
IT administrators can set up their newly onboarded devices with basic settings to boot them for corporate usage. This process is called device provisioning. With Endpoint Central, IT administrators can provision their newly added computers and mobiles using the features namely Configurations and Profiles.
How to deploy a configuration?
Configurations are applicable to your desktops, laptops and servers. Configurations can be distributed to endpoints running on Windows, Mac, and Linux. Endpoint Central supports 50+ configurations across the operating system listed above. Visit this page to know more about configurations.
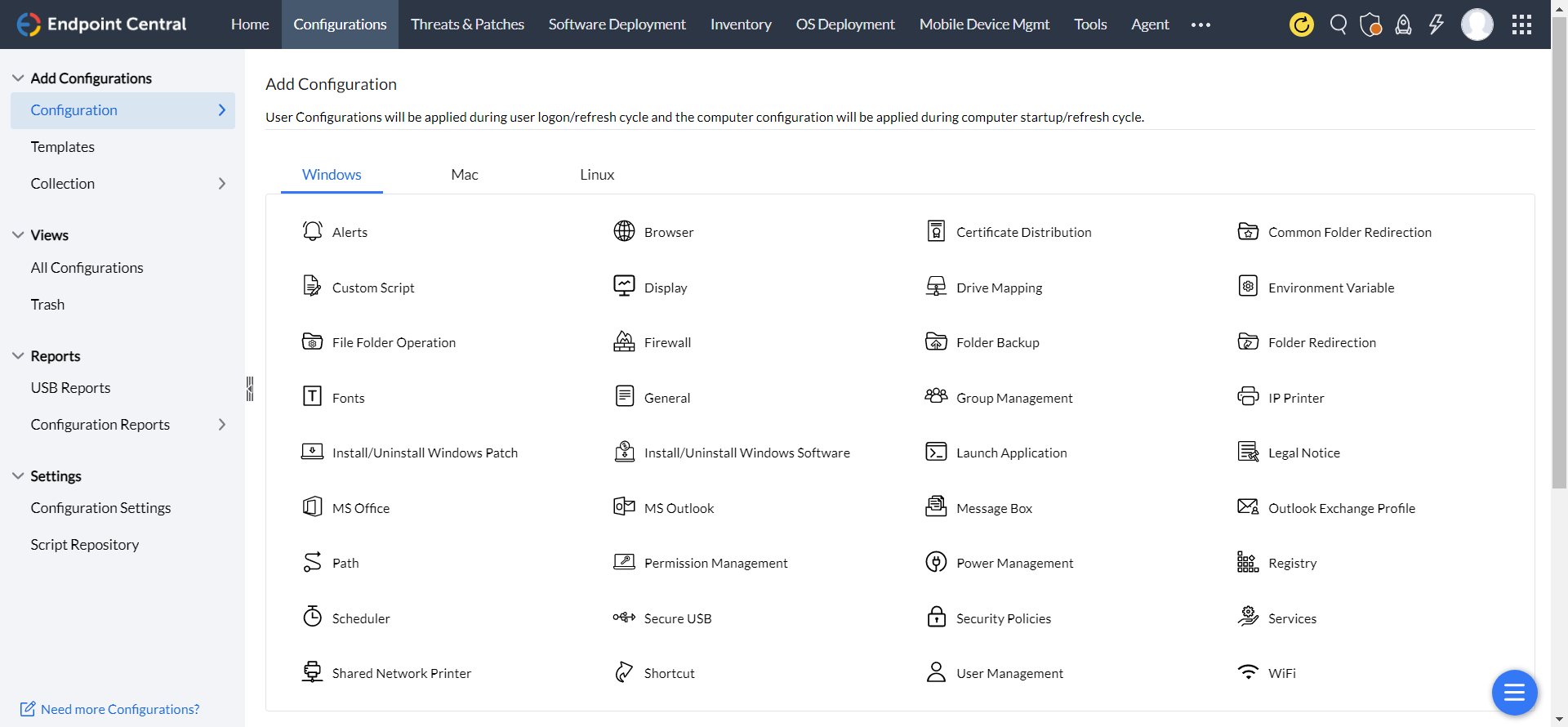
How to deploy a profile?
Profiles are basic settings available for your mobile devices and modern laptops. IT administrators can provision their Android, Apple (Mac, iOS, and iPadOS), Chrome and tvOS with the profile management.
3. Threats and Patches
Threats refer to vulnerabilities that can compromise the security and functionality of the system. These threats can take up many forms and can break into the systems in different ways. To safeguard endpoints against any kind of security threats, patches are developed by software vendors or developers on a day to day basis. Patches refer to software fixes or updates that can fix any kind of vulnerabilities in the system. The need for patches arises because no software is perfect and vulnerabilities can be discovered over time. Threat actors often attempt to exploit these vulnerabilities to gain unauthorized access, steal information, or disrupt systems. Patches are crucial for maintaining the security and stability of software and protecting users from potential threats.
Vulnerability Assessment
With a highly efficient vulnerability assessment system, Endpoint Central provides a risk basis diagnosis framework to mitigate different kinds of security threats that can destruct the functionality of the system. The pro-active diagnosis of zero-day vulnerabilities can help you discover gaps or flaws in applications or operating systems. The security configurations that come with this feature make sure that all your endpoints are secured. You can also enable the end-of-life software feature to detect software that is no longer supported by vendors, which can pose a great threat to all the endpoints in your network.
Patch Management
The patch management feature of Endpoint Central is known for its extensive ability to offer patches according to the severities found in your network. The automated patch management feature not only ensures security in your network but also ensures proper utilization of resources and conserves crucial time spent on manual patching of systems.
4. Real Time Asset Management
What is IT Asset Management (ITAM)?
IT Asset Management (ITAM) is the practice by which IT administration team can track, monitor, and utilize the IT assets effectively throughout it's lifecycle, right from onboarding till retirement. The asset management capabilities of Endpoint Central allows IT administrators to perform actions such as scan the managed assets, audit them with the inventory reports, analyze and trigger alerts to track any suspicious movements, hardware asset management, software asset management, basic security auditing, and compliance.
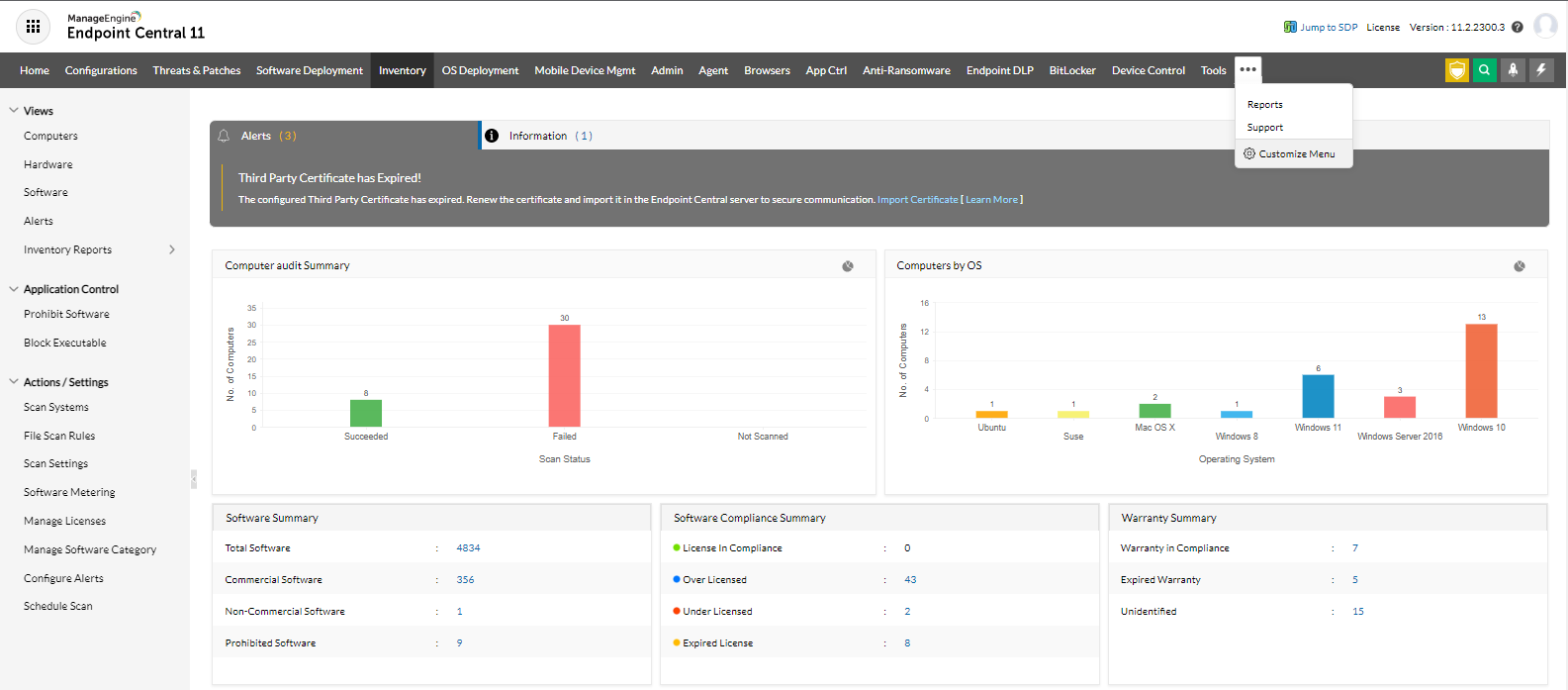
How to setup IT Asset Management in Endpoint Central?
Endpoint Central provides a user-centric approach to your IT asset management needs and here is a step by step guide, that will help you to setup and start working on your IT auditing, Asset Management and achieve compliance.
IT Inventory
- Inventory Scan
- Schedule an Inventory Scan
- Inventory Scan Settings
- Inventory Alerts
- View Alerts
- Custom Fields
Inventory Details
- Inventory Details
- Hardware Details
- Computer Details
- System Details
- Software Details
Software Asset Management
- Software Metering
- Software License
- Prohibit Software
- Block Executable
- Software Category
- Software Grouping
Inventory Reports
- Inventory Reports
- Hardware Reports
- Software Reports
- Software Compliance Reports
- System Details Reports
- Warranty Reports
5. What is application management and control?
The application management and control feature in Endpoint Central provide the ability to monitor, control, and manage applications on endpoint devices like servers, desktops, laptops, tablets, PoS devices and mobile devices from a centralized location. This allows organizations to enforce security policies, streamline software deployment, and ensure compliance throughout their network.
What are the features of application management and control?
The key aspects of application management and control in Endpoint Central include:
- Software Distribution: The distribution of software can be accomplished through two methods: pre-filled templates, which are suitable for most non-commercial software, and the manual package creation flow, which is used for distributing in-house software and commercial software. These methods cater to Windows, Mac, and Linux operating systems.
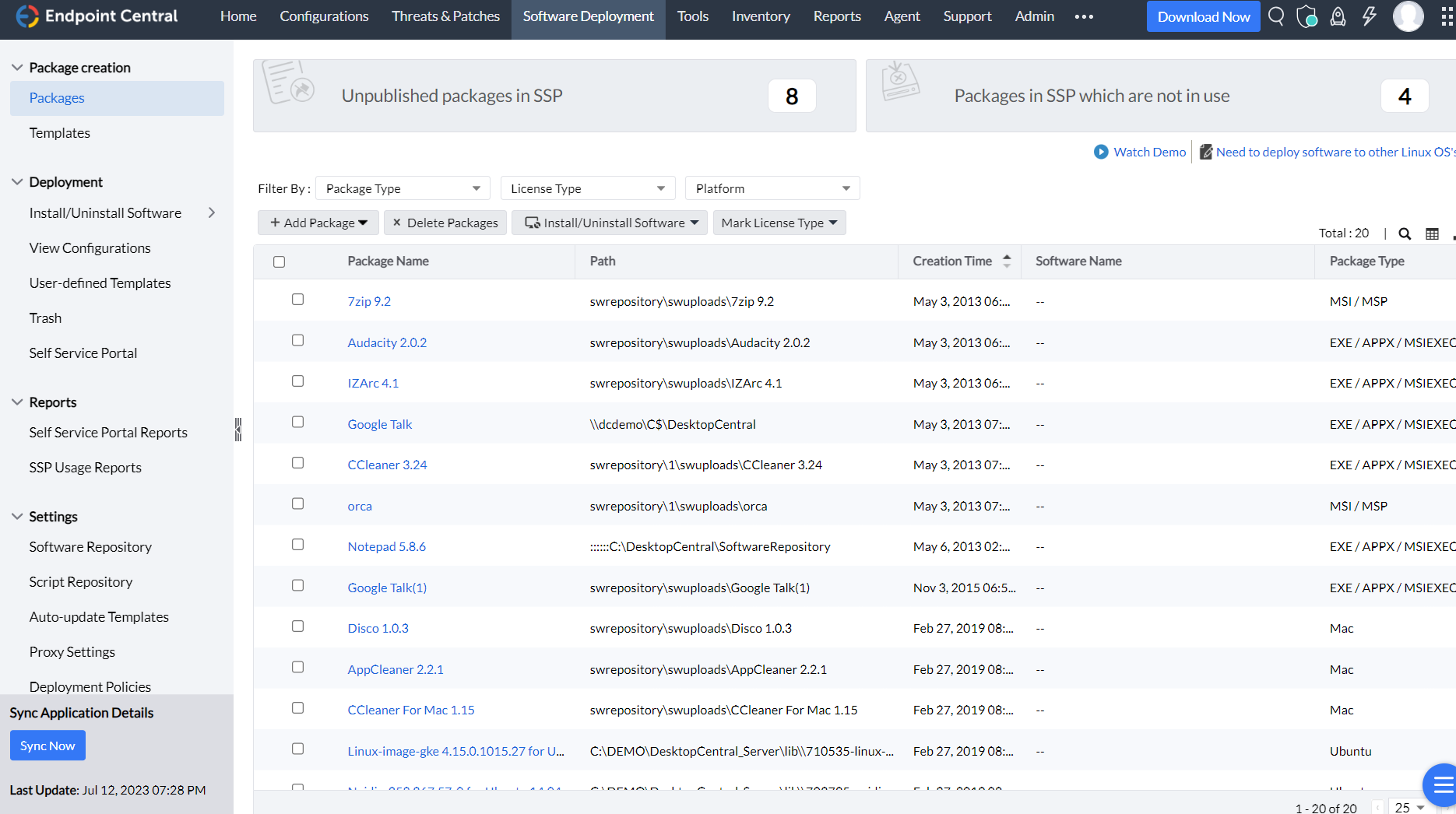
- Application management for modern devices: Application management encompasses the management and deployment of applications across various devices, including Android, Apple, Chrome, and PoS (Point of Sale) devices. This includes both store apps, available through app stores, and enterprise apps specifically developed for organizational use.
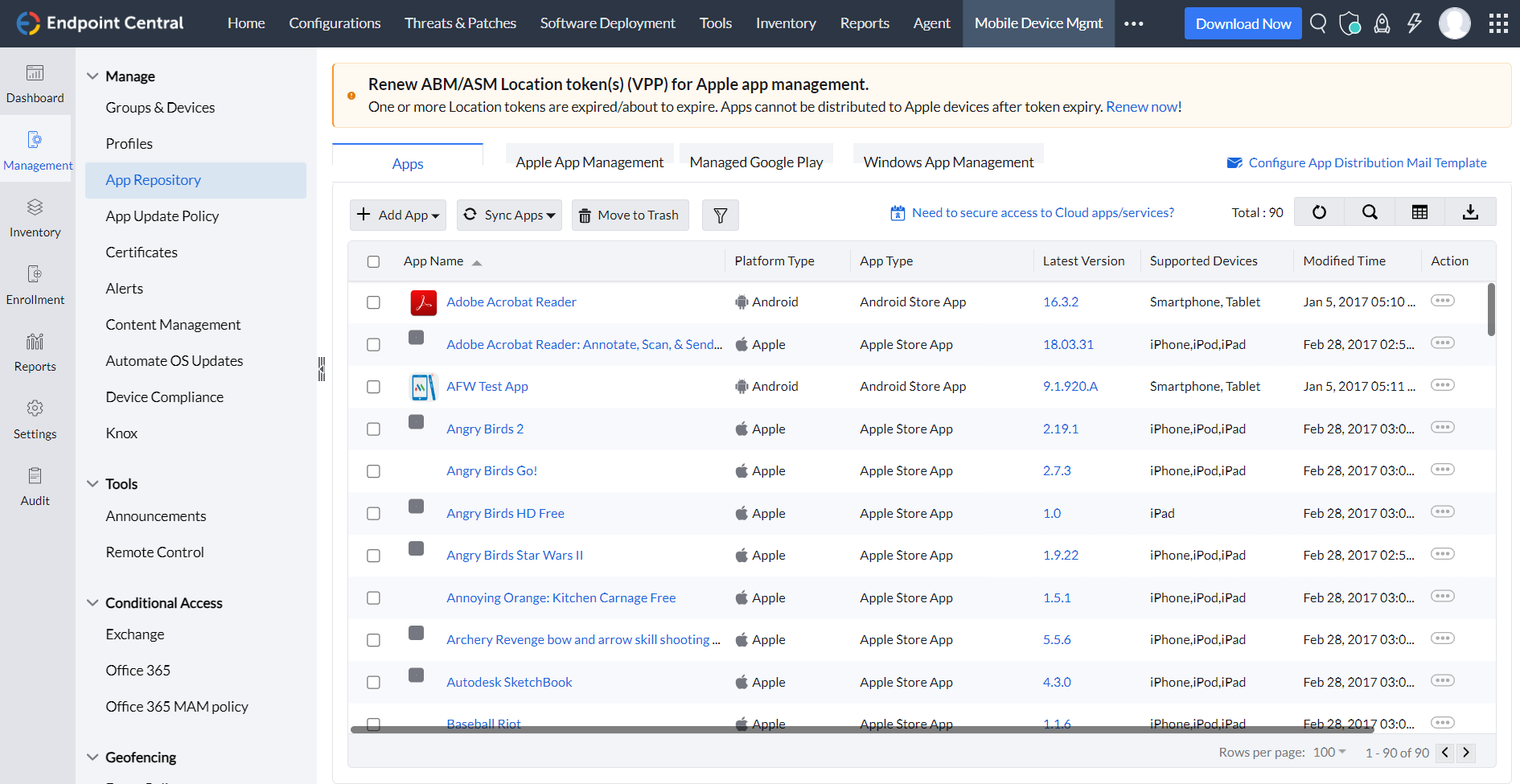
- Restricting unauthorized applications: Application control provides assurance and control when managing a fleet of applications within an IT network. It enables administrators to restrict or allow the usage of applications based on specific parameters. This ensures a higher level of security, compliance, and efficient management of applications across the network.
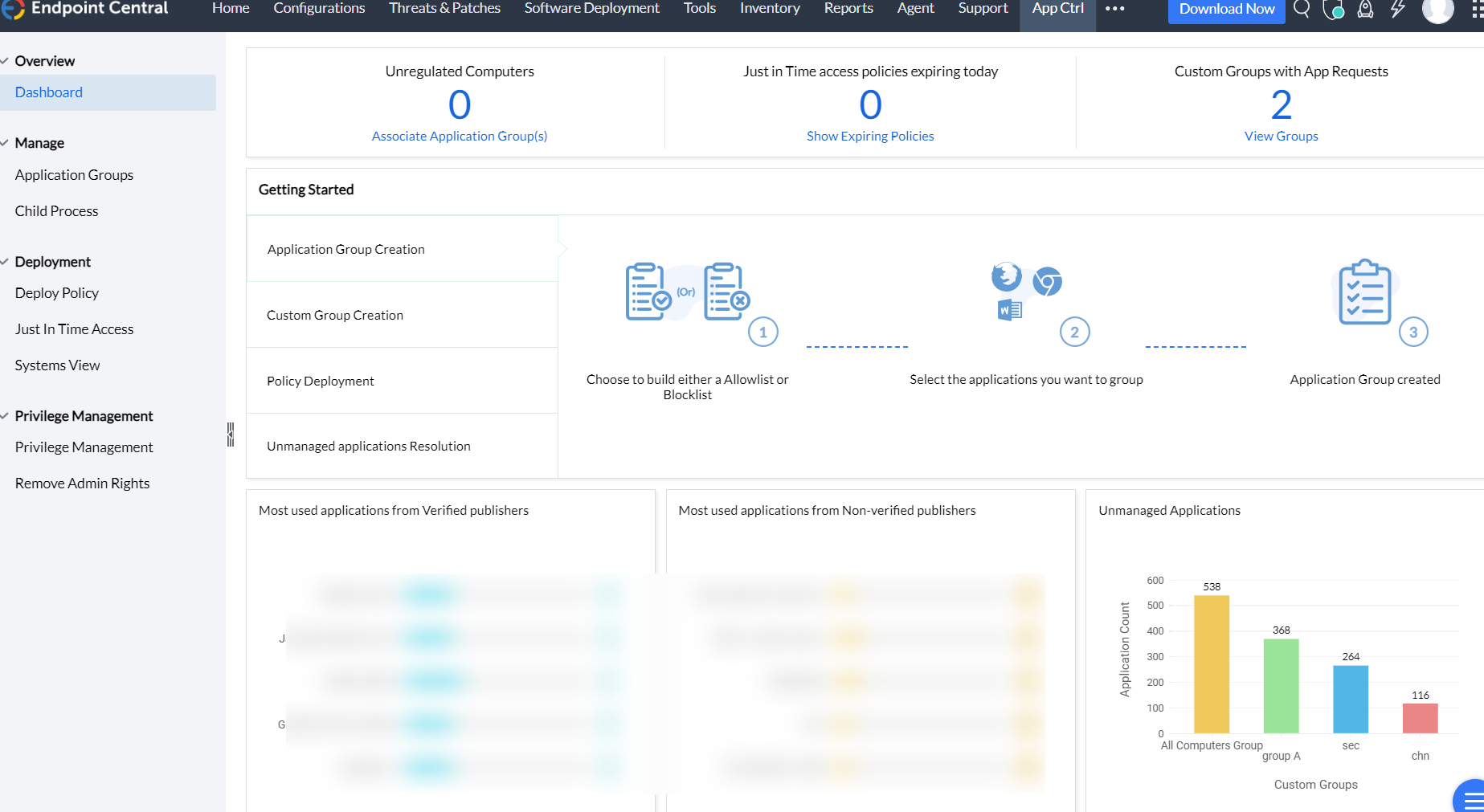
6. Endpoint Central Tools
Endpoint Central offers a wide range of tools that come in handy for IT administrators on any given day. With the help of tools, you can perform a variety of operations that simplifies the entire process of remote troubleshooting. Refer to the OS comparison matrix to know more about the features supported for specific operating systems (Windows/Mac/Linux).
The following tools are offered by Endpoint Central:
- Remote Control
- System Manager
- Remote Shutdown
- Wake on LAN
- Chat
- Announcement
- Windows System Tools
7. OS imaging and deployment
Imaging
- Online Imaging
- Offline Imaging
- PE Media Creation
- Hardware Independent Deployment
Customizing Deployment
- Creating Deployment Template
- Post Deployment Activites
- Adding Applications
Deployment
- Deployment via Task
- Deployment via Template
- Zero-touch Deployment
- Instant Deployment
Remote Deployment
- Booting & Deployment
- OS Deployment Settings
8. What are reports?
Endpoint Central helps IT administrators to generate reports on their managed IT network and present it for audit and achieving compliance. Endpoint Central has an over-arching reporting capabilities which can be used to generate reports based on multiple combinations and collaborate with adjacent teams.
What are the types of reports?
Endpoint Central categorizes its reporting on the below defined criteria:
- User-defined Reports
- Schedule Reports
- Custom Reports
- Query Reports
- Active Directory Reports
- Group Reports
- Computer Reports
- GPO Reports
- Domain Reports
- OU Reports
- Security Reports
- Application Control Reports
- BitLocker Reports
- Browser Reports
- Device Control Reports
- Vulnerability Reports
- Vulnerable Patches Reports
- Patch Reports
- Supported Patches Reports
- Self-service Portal Reports
- Configuration Reports
- Task Reports
- Power Management Reports
- USB Reports
- Inventory Reports
- User Log-on Reports
- MDM Reports
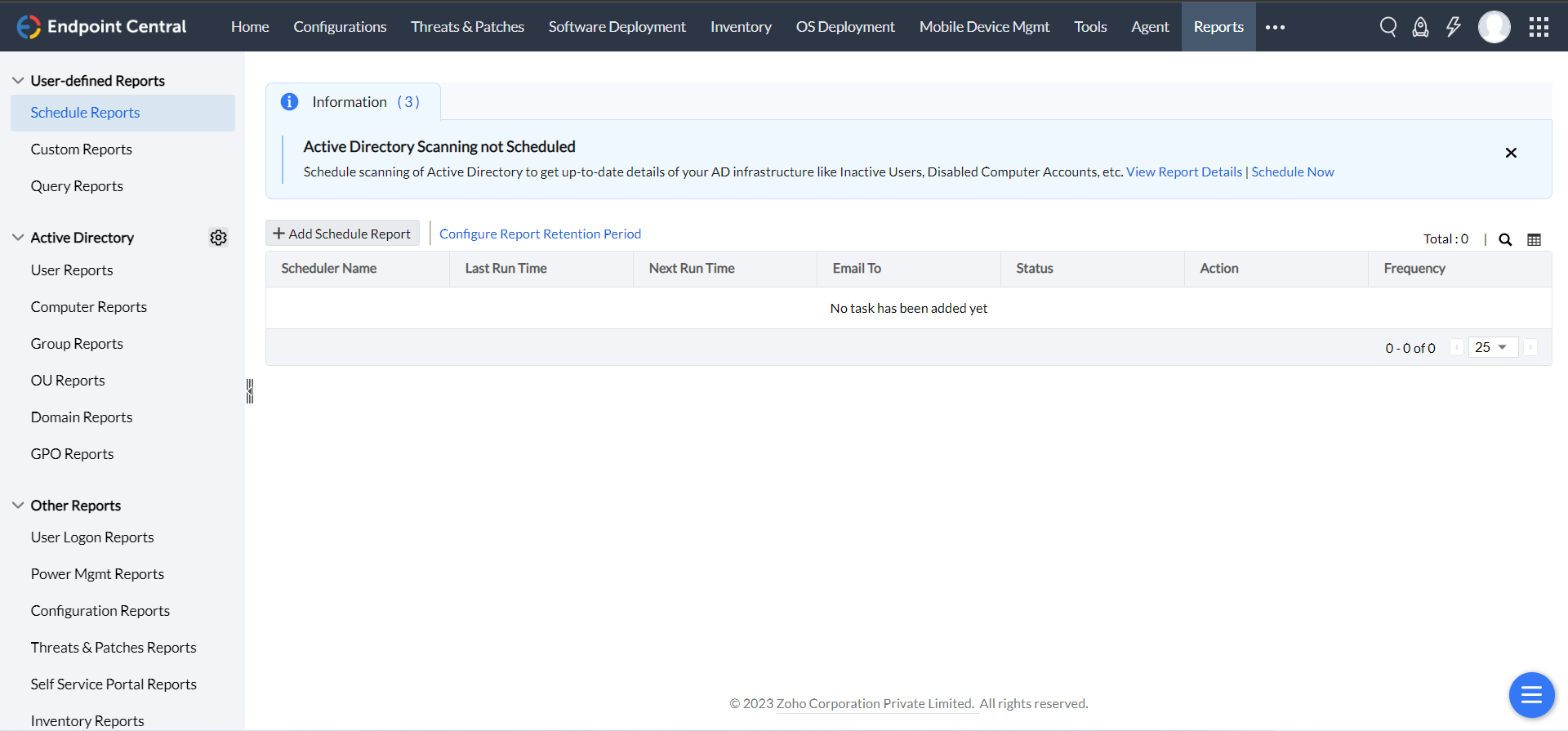
How to setup reporting feature in your network?
Reports can be accessed in the web console by the authorized users. IT administrators can generate reports from this view by picking the required type and filter.
9. Endpoint Central Integrations
What is Endpoint Central?
Endpoint Central is a unified platform for endpoint security and management operations. Endpoint Central provides a user centric approach for IT administrators to secure and manage endpoints that are running on Windows, Mac, Linux, Android, iOS, iPad OS, tv OS, and Chrome OS. Furthermore, Endpoint Central can manage devices such as desktops, laptops, servers, Mobile devices, Point of sale devices, tablets, and rugged devices. In addition to endpoint administration tasks, Endpoint Central offers integrations with adjacent IT solutions for maximum ROI.
Why do you need Endpoint Central Integrations?
Endpoint Central can be integrated with a number of IT tools to exceed the maximum efficiency of IT administration. With an integrated setup, IT teams can yield the following benefits:
- Collaborate between teams easily thereby breaking down the siloed approach to resolution and also remediate tasks/issues easily.
- Pronounced visibility and control on your IT network.
- This approach also provides a proactive approach to IT management and security.
- Implement a centralized approach to your IT administration tasks.
What are the integrations supported?
To reap the benefits stated above, Endpoint Central supports the following integrations:
- IT Service Management
- ManageEngine ServiceDesk Plus
- Jira
- Spiceworks
- Freshservice
- ServiceNow
- Zendesk
- Enterprise Protection Platforms
- Tenable.io
- Tenable.sc
- Business Intelligence
- ManageEngine Analytics Plus
- IT Asset Management
- ManageEngine Asset Explorer
- Integration Platform as a service
- Zoho Flow
10. How to create BitLocker policies to secure enterprise data?
Data encryption must be highly prioritized in an enterprise network. For businesses with vast number of machines, it will be difficult to manually enable BitLocker. This is where the BitLocker module in Endpoint Central serves as a solution to manage and secure your drives.
Create policies for BitLocker drive encryption for machines within your network to secure your data. The BitLocker module in Endpoint Central enables you to build flexible policies to encrypt your drives according to your machine's requirement.
How to create an encryption policy in the BitLocker module?
NOTE - Adhere to BitLocker encryption pre-requisites before deploying an encryption policy.
- Navigate to the BitLocker module on the Endpoint Central console -> Policy Creation -> Create Policy
- Provide a name for your policy and if needed, add a description.
- Toggle the option Drive Encryption
when this setting is enabled, the drives will be encrypted
Once the setting is enabled, the BitLocker policies allow you to access and choose encryption settings for machines within your network.
Protect your machines with Authentication.
The BitLocker policies help you to secure your machines with authentication. The authentication type varies for machines with TPM and for machines without TPM.
Authentication Type for machines with TPM
Authentication for machines with TPM can be enabled by choosing any of the three options provided as shown in the image.
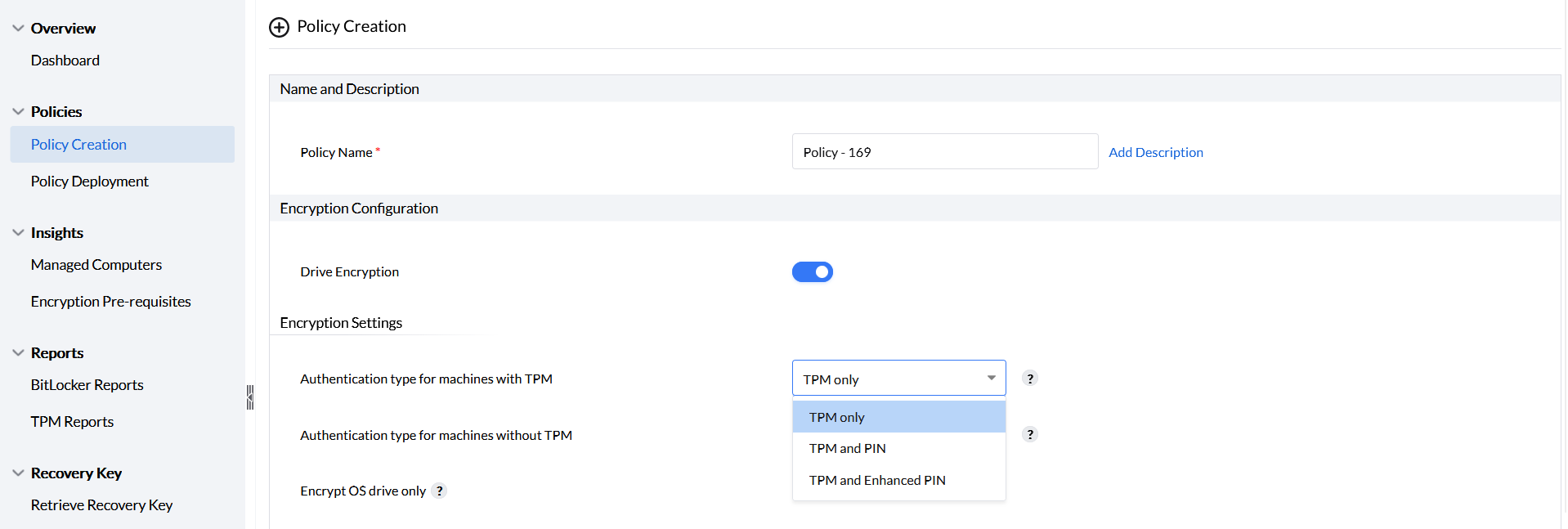
- TPM only : The drives will be unlocked with TPM authentication, no user input is required to unlock the drives.
- TPM and PIN: In this case, TPM authentication is followed by PIN authentication. PIN authentication can contain only digits and the maximum length is defined to be 6-20 characters (digits). The PIN must be provided upon boot.
- TPM and Enhanced PIN: In this case, TPM authentication is followed by Enhanced PIN authentication. Enhanced PIN authentication can be a combination of alphanumeric and special characters. The maximum length is defined as 6-20 characters and must be provided upon boot.
Authentication type for machines without TPM
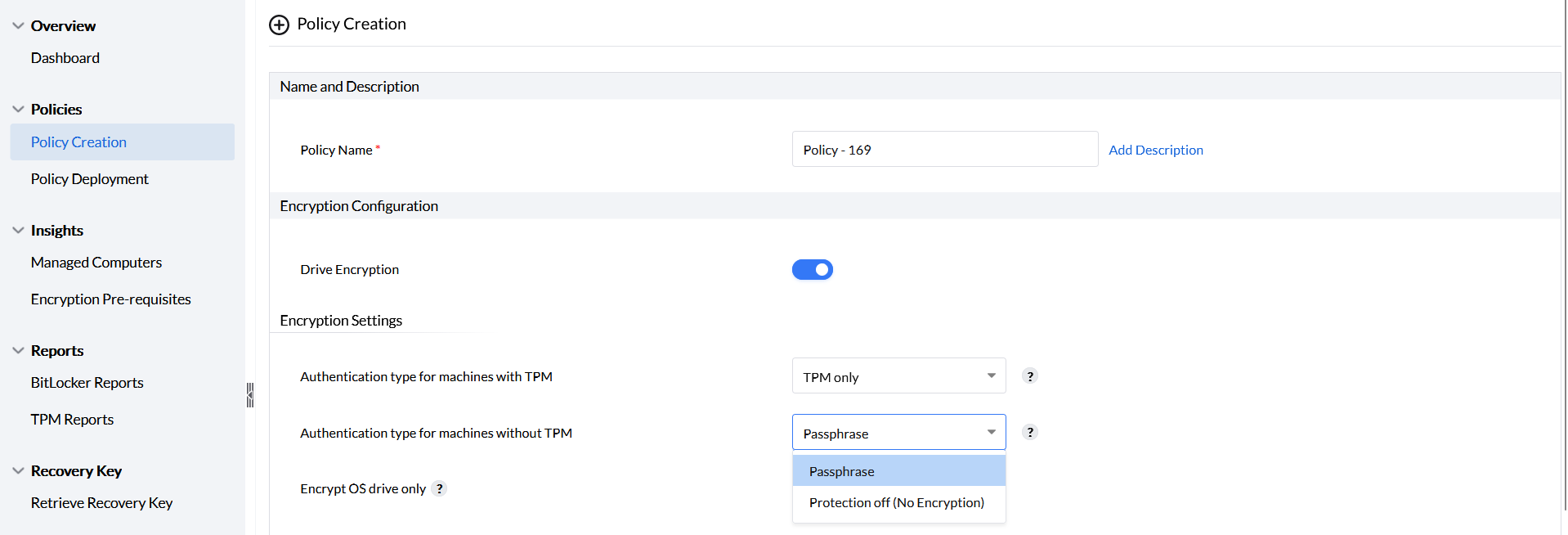
Authentication for machines without TPM can only be enabled with the passphrase option. This will prompt the user to enter a passphrase every time the computer is started.
Encryption of your drives can be optimized with the encryption settings provided by the BitLocker policies. You are provided with three encryption policies where you can apply policies by combining them if required.
- Complete encryption of drives.
- Encryption of OS drives.
- Encryption of used space in your drives.
Complete Encryption of drives.
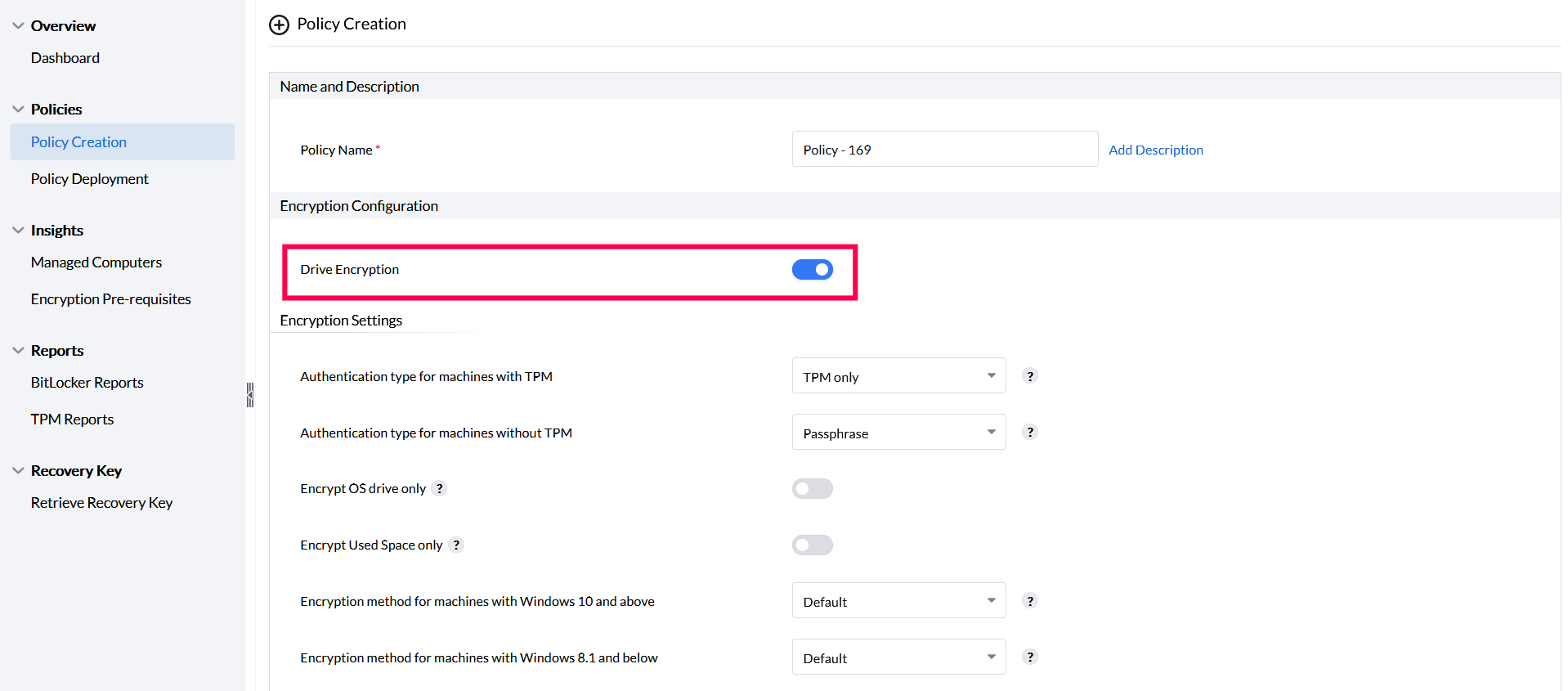
For full space encryption, enable only the Drive Encryption setting.
- Ensure that these options are disabled: Encrypt OS drive only and Encrypt used space only.
- By default, by enabling only the Drive Encryption option, all drives and spaces will be fully encrypted.
Encrypt OS drives only
To encrypt only the OS drive, enable the option Encrypt OS drive only in the Encryption Settings section.
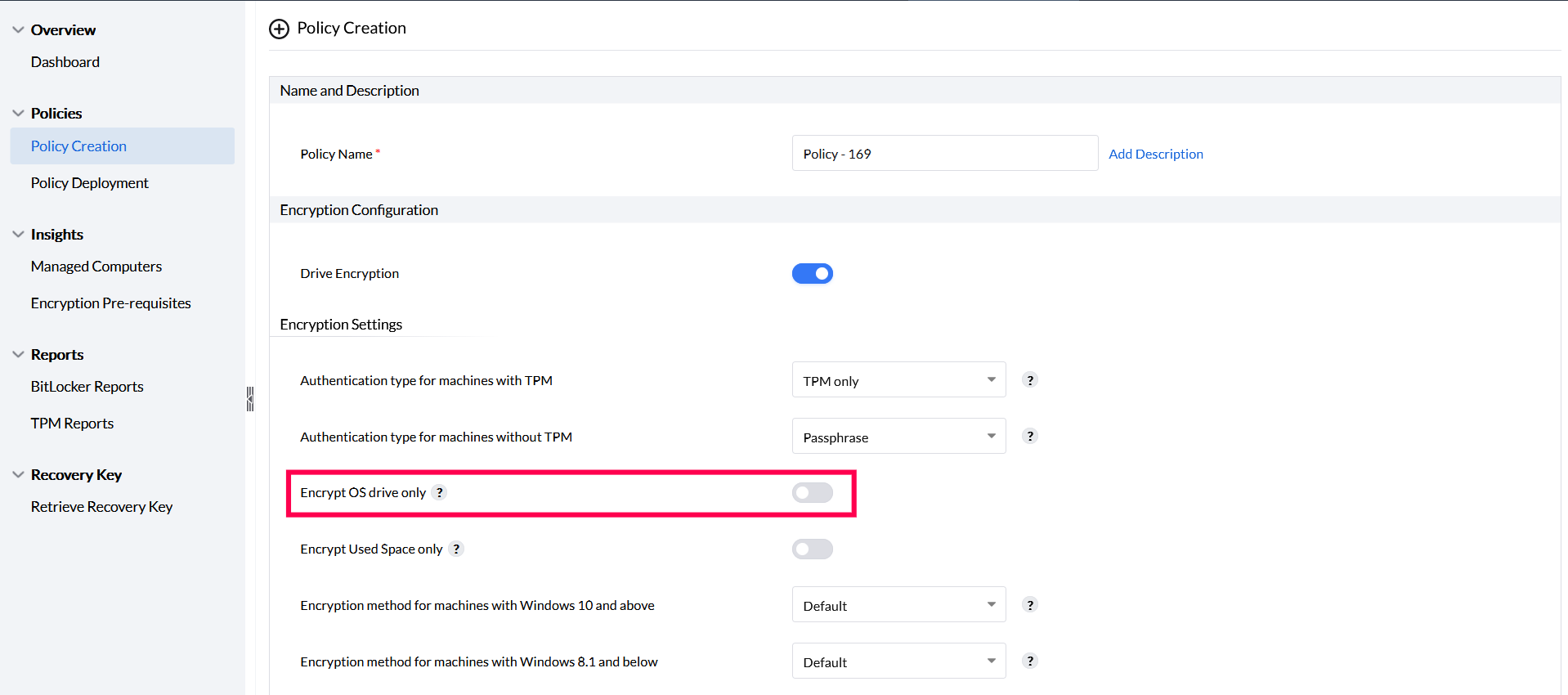
This will ensure that all volumes in the OS drive are encrypted and that all other data drives will be or remain decrypted.
Encrypt used space only
To encrypt only the used space, enable the option Encrypt used space only in the encryption settings section.
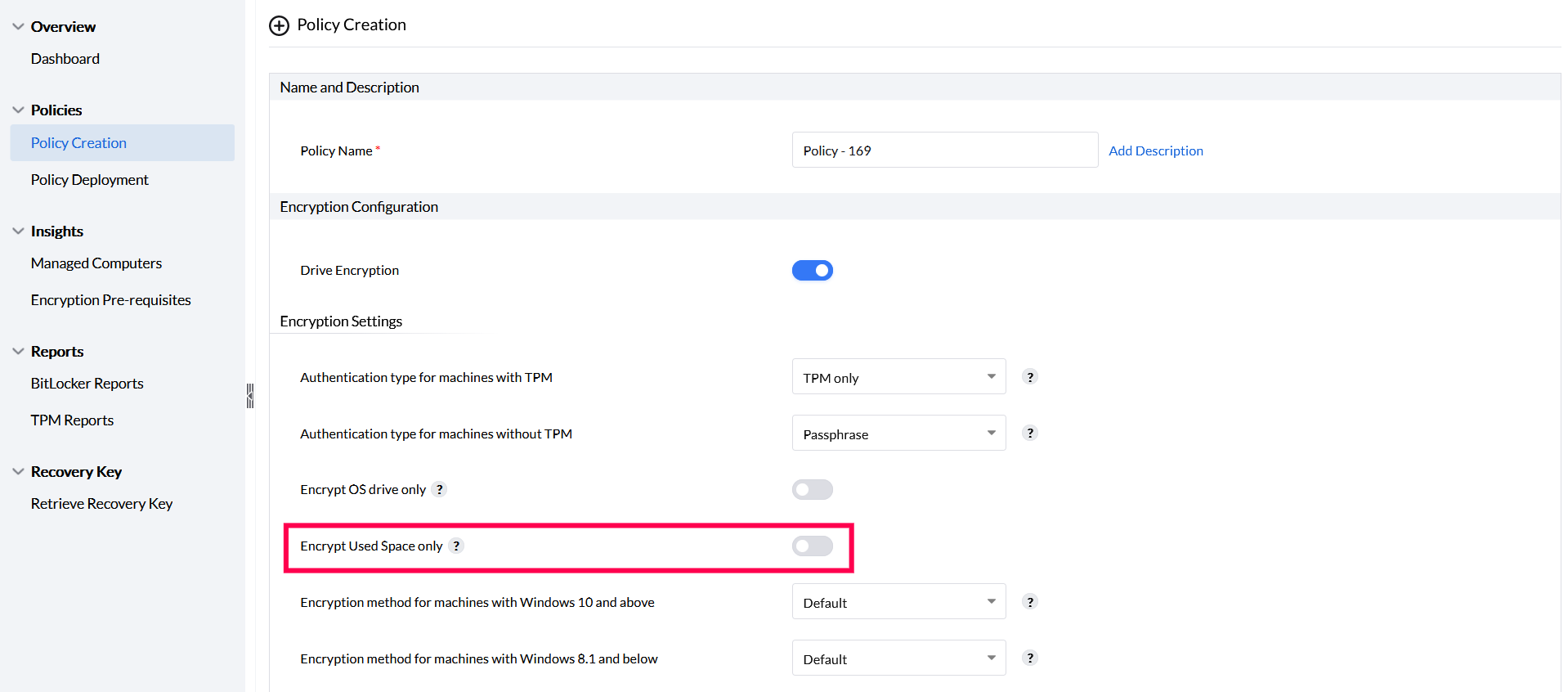
This ensures encryption of only the used space in your drives while the free space available on your drives will be or remain decrypted.
BitLocker gives you additional settings on how to encrypt your machines with different encryption methods. There is a specific set of encryption methods that are available for machines with Windows 10 & above and for machines with Windows 8.1 & below. The default method would be either the method previously configured using GPO or the encryption method already associated with your system OS
Encryption Method for machines with Windows 10 and above
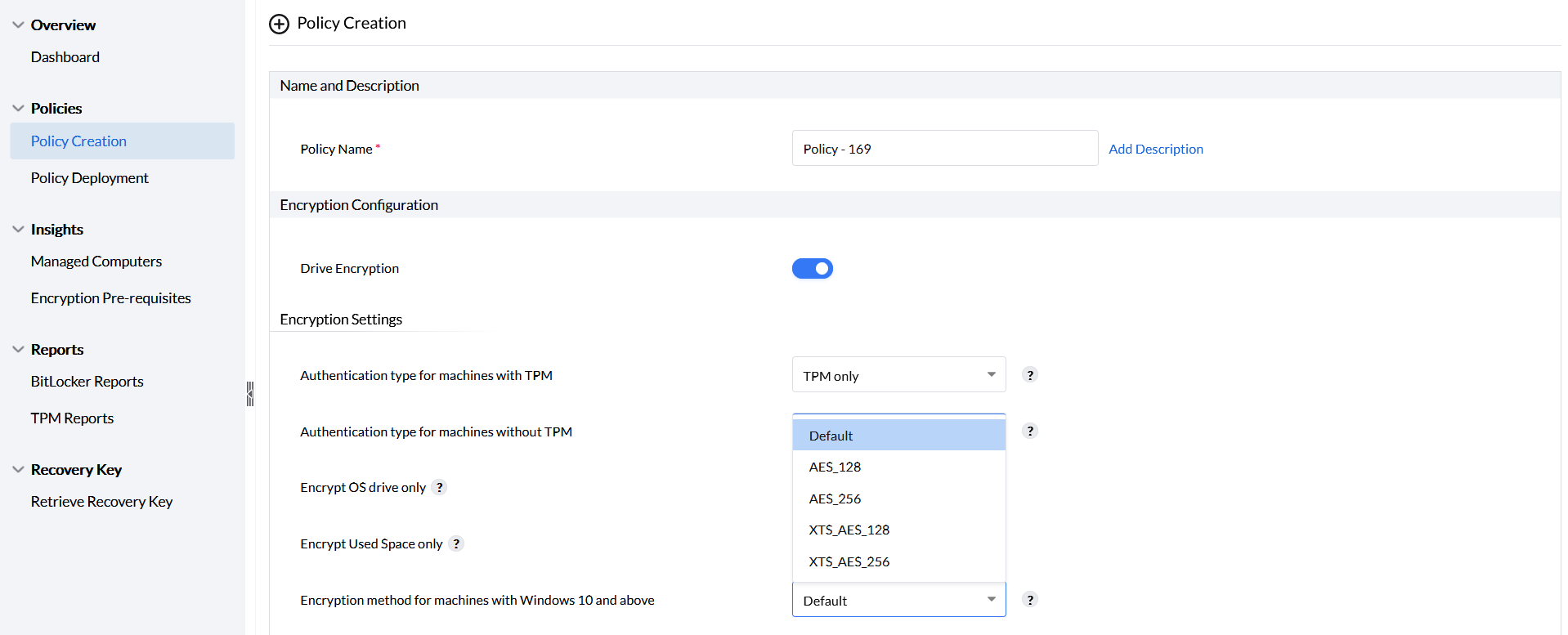
The encryption methods available in this drop down are applicable.
Encryption Method for machines with Windows 8.1 and below
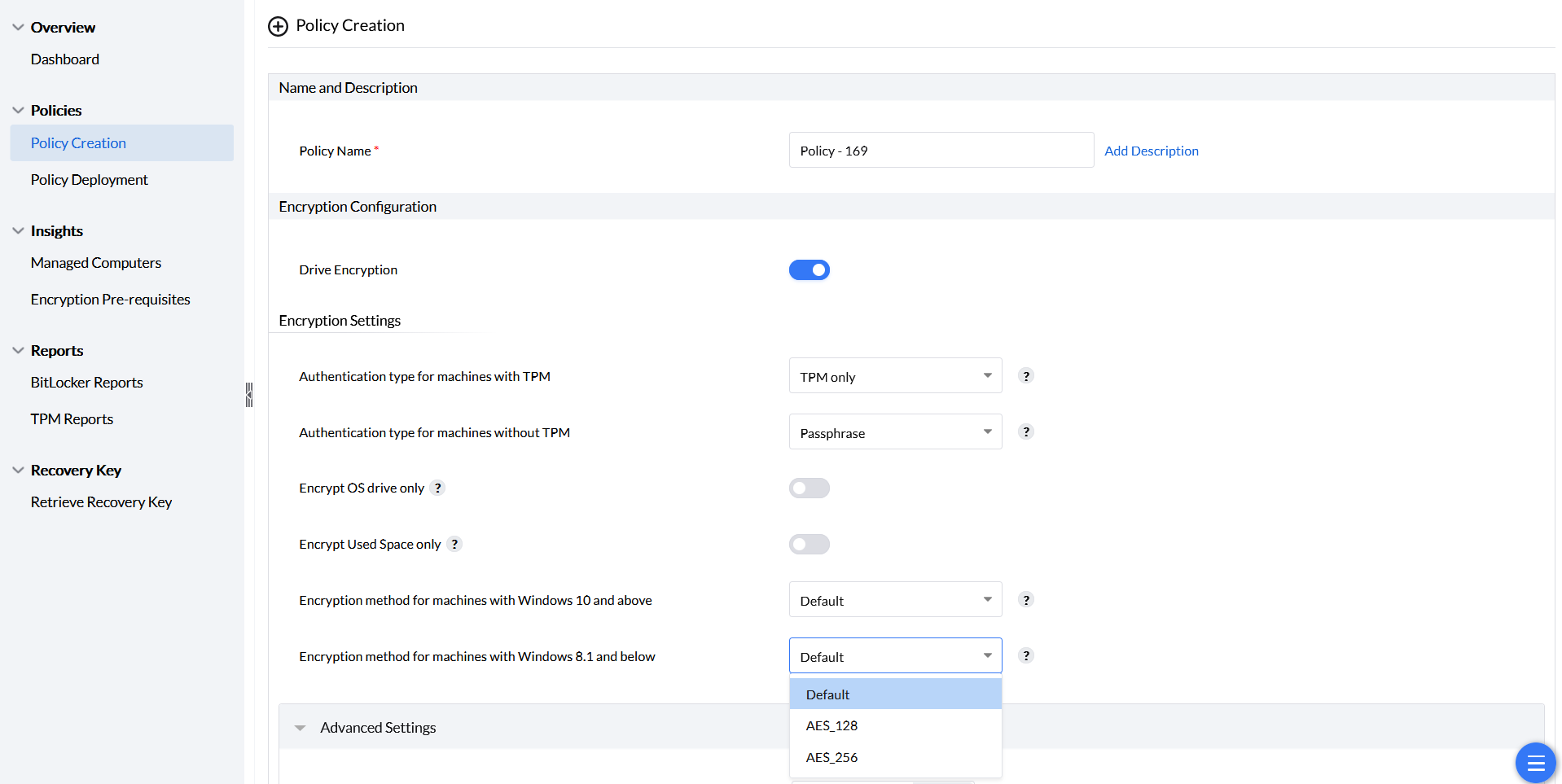
The encryption methods available in this drop down are applicable.
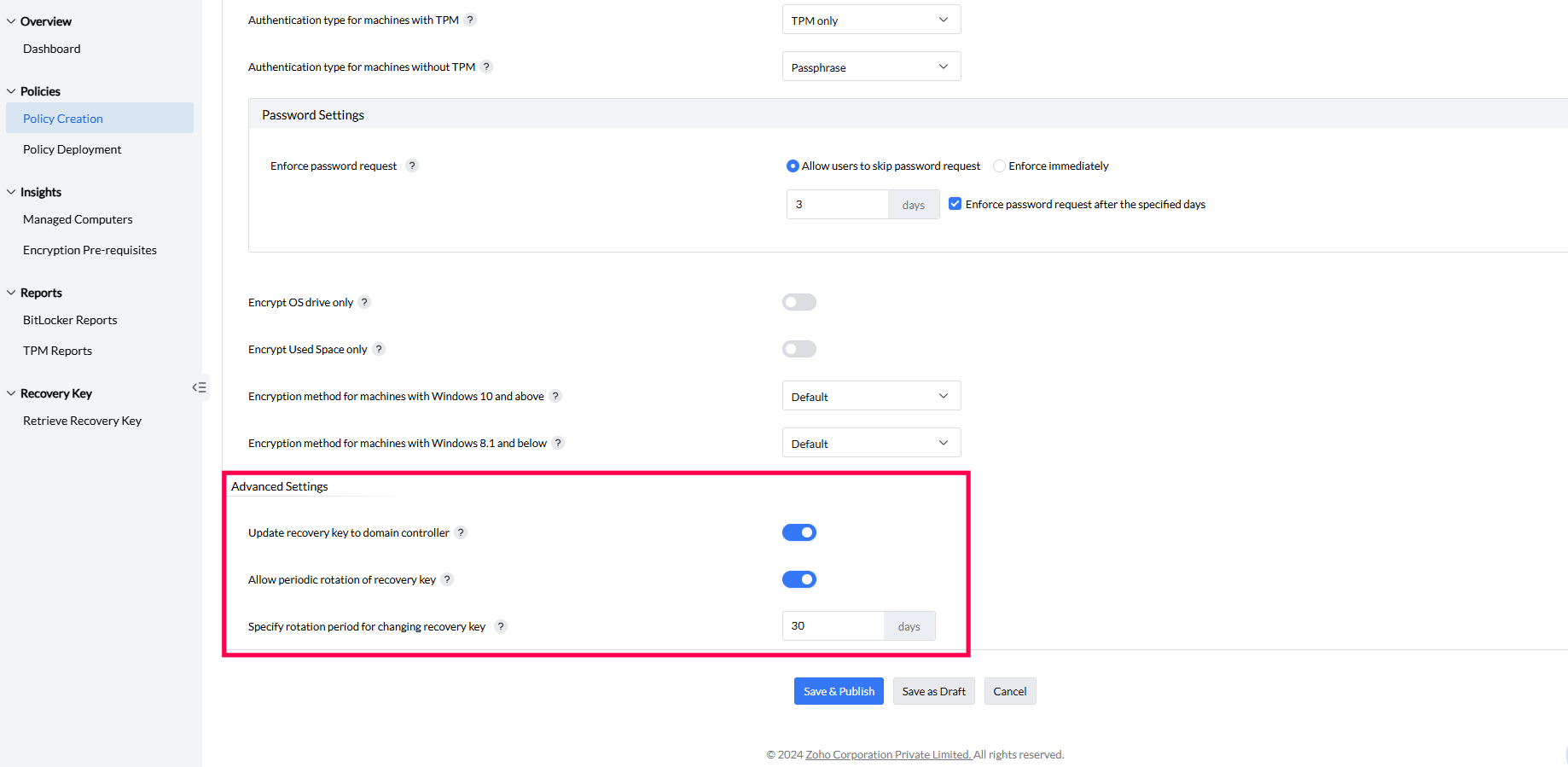
Advanced settings
The BitLocker policies contain advanced settings where you can postpone restart, configure recovery key update and rotation period.
- Allow users to postpone restart: For successful BitLocker encryption, your machines have to be restarted. You can allow the user to postpone the restart for a certain number of days. Once this specified duration expires, the computer will be automatically restarted and the encryption process will begin. Note: In the latest versions of Windows, restart is not required wherein the encryption process automatically begins.
- Update recovery key to domain controller: Once a new recovery key is generated, you can update it to the domain controller by toggling the option Update recovery key to domain controller. This ensures that a consolidated list of latest recovery keys will be maintained in the Active Directory. If the option is disabled, the list of recovery keys will only be available in the product server.
- Allow periodic rotation of recovery key: On toggling this option, Specify rotation period for changing recovery key opens. As an added safety precaution, specify a rotation period after which the old recovery keys will be replaced with new ones. After the specified number of days, the new recovery keys will be updated automatically.
Once the above mentioned settings have been configured according to your requirements, you can save as a draft or save and publish directly.
11.How to control devices with Endpoint Central's device policies?
- On the product console --> Go to Create Policies
- Click create.
- Select the type of access you want to give for each device type. You can select 'allow' to allow the device to access your endpoint else you can select 'block'. If you want to retain the existing status, select 'No change'. If you want to allow only the trusted devices of the corresponding type, you can also directly select 'allow only trusted devices'.
Configure audit settings.
- Enable the toggle against Monitor all device activities.
- Specify the frequency (in hours) at which the reports should be generated.
- Enable the toggle against 'Send blocked device details' to receive details on the blocked devices that attempted to connect with your computer.
Configure Alert settings.
Select any one of the alert types available under the Alert settings.
Notification OFF.
- You can select this option when you do not want to alert the end user during an unauthorized access from their end.
Default Notification.
- You can go ahead and select this option when you have a default message that is to be displayed to alert the end user whenever there is an unauthorized access from their end.
Custom Notification.
- You can select this option when you want to display a customized message to alert the end user when there is an unauthorized access from their end.
12. What is browser restriction?
Browser restriction is used to restrict the access of certain websites and web applications to specific browsers and devices. This can be done to ensure the best user experience, the highest security, or to prevent certain features from being available on certain browsers.
Benefits of Browser Restriction in your organization
Thanks to teleworking, browsers today have become a significant part of employees' day-to-day business. With a number of different browsers out there, and each of these browsers offering their own set of features, it's hard for IT admins to manage them, in terms of both security and employees' productivity. While some of these browsers focus on security of users, some prioritize user-experience. While most web-applications work fine across most browsers, some might not do so in specific cases. Depending on which browser the employees' use, they might experience breaks in certain web-applications leading to an increase in help-desk calls. This is a hassle for both IT admins and their employees.
Browser Restriction with Endpoint Central.
With Endpoint Central browser restriction feature, IT admins can mandate the usage of a single browser by their employees. They can test out the functioning of mission-critical web-applications in their selected browser and mandate its usage to ensure that employees' user-experience remains intact. Mandating the usage of a single browser also helps IT admins weed out vulnerabilities and ensure the security of the mandated browser.
No comments:
Post a Comment